Now a days, hacking gmail account is increasing. Most of people doesn't know how to be secure(because they doesn't visit BreakTheSecurity). So please refer our website to your friends as Security tips Blog. Ok let me come to the point. In this article, i will explain how to recover your hacked or compromised gmail accounts.
First of all verify yourself whether your entering the correct password. Also check whether the caps lock is turned on.
How to Recover Your Gmail Account?
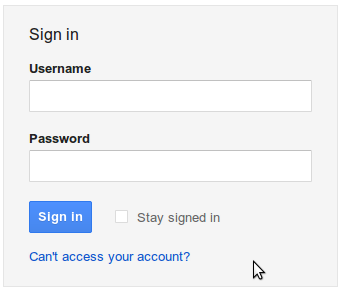
If you believe your account is hacked, then visit click the Can't access your account? link below the signin button in gmail.
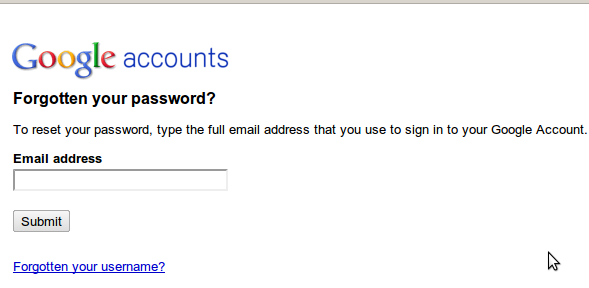
Enter the Email address . it might ask for CAPTCHA ,fill it and continue.
option 1: If you have secondary email address, select secondary mail and ask to send the password to your secondary mail address.
option 2: Answer to your security question and change the password
option 3: if you have added mobile number in your account. then you can recover through mobile.
Contact Gmail:
If the above option doesn't work for you? then you have to contact the gmail.
Visit
https://www.google.com/support/accounts/bin/request.py?ara=1
It will ask whether the password recovery option worked or not. Click "No" button. It will ask you to enter the information about your email account. Fill everything. They will ask to enter the email to contact you, enter the alternative email address that you have.(if that also hacked, then create new account and enter it).
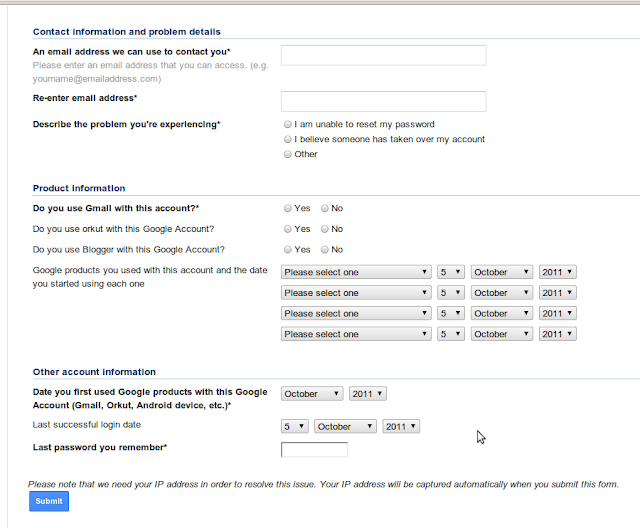
Submit the form.
They will contact you soon.
FAQ About Account Recovery
Q. Why can't I tell someone private information about my account that they could look up to verify my claim?
A. Account privacy rules are very strict within Google, and allowing employees to look at the contents of an account would be a serious breach of privacy.
Q. Why isn't there a comments section on the Account Recovery Form where I could add additional information to prove my claim?
A. Like above, it would be a violation of account privacy for an employee to look in the account to verify any additional information supplied.
Q. Why can't I simply talk to somebody about this?
A. Unfortunately, Google does not offer live support for the free Gmail product (see: http://mail.google.com/support/bin/request.py?contact_type=contact_policy). You must use the recovery methods provided.
Q. Why can't Google lock the account to protect it from any more damage or outgoing spam.
A. They will lock an account that the detection system identifies as being compromised and sending out spam. But again, privacy concerns would prevent them from simply locking an account because someone claims it's theirs and is compromised. In addition, since there is no live support, there is no one to even make such a request to.
Q. I had a really long password of random strings that would be impossible to guess. How was my account compromised?
A. Google (as most e-mail providers) have blocks to prevent trying lots of passwords to guess the correct one (brute-force attacks). Most accounts are compromised by harvesting passwords other ways. While a secure password is important, it's only one in a long list of things needed to keep any online account secure.
Q. But I'm very careful with my password. I don't give it to anyone except an official request from Gmail.
A. Unfortunately if you provided your password in response to any e-mail (even claiming to be from Google/Gmail) then your password was harvested by phishing. It's very common, and can trick even the most careful people.
Q. My contacts were deleted by the hacker, how do I recover them?
A. Deleted contacts can now be restored to any point in the last thirty-days: http://mail.google.com/support/bin/answer.py?hl=en&answer=1069522
Q. My e-mail history was deleted by the hacker, how do I recover it?
A. Have you looked in All Mail and Trash for the missing information? Have you used Search to try and find it? Unfortunately, messages deleted from Trash or Spam can not be recovered. If you would like to request Google attempt to recovery messages deleted by a hacker, see: http://mail.google.com/support/bin/answer.py?hl=en&answer=8256
Q. My account was deleted by the hacker, can I recover it?
A. The Account Recovery Form can sometimes restore a recently deleted account. That is your only option in this case.
Q. I don't care about the account, can I just get the e-mail history or the contacts from it.
A. Unfortunately, you have to be able to access the account in order to transfer any information out of it. This means you need to try and recover the account.
Q. I don’t care about the contents, I just need the e-mail address back because I have other things linked to that address.
A. Account names are never re-used, so you can’t re-create the account. So to get the name back you will have to try and recover the account.
Q. Can I find out who did this? Can anyone prosecute them?
A. About the only information you have available is the list of the last 10 IPs to access your account (see the Details link below the Inbox). But given how easy it is to fake IPs, and how inaccurate they are, it's unlikely that more than a general location can be determined. In general, law enforcement is not interested in a simple compromised account, and Google is not a law enforcement agency. Bottom line is: one's energy is better spent on recovery and re-securing the account.
Q. Isn't what the person did illegal? Can I sue them or get them arrested?
A. Any legal questions should be asked of local law enforcement or an attorney. Google is neither of those and can not advise you on any actions.
Q. Can I find out what they did in my account while they had access.
A. There are no account activity logs available, so you can’t find out for sure. If there is spam in your Sent Mail, they you know they used the account for that. But there’s no way to know if or what messages they may have looked at, so take appropriate precautions.
Q. How was my account compromised?
A. There are many ways passwords can be harvested and account compromised, but the most common ones include:
- Using the same password on multiple web-sites. A less secure site is hacked and they get the user database (e-mail and password) and then just try them all. If the person did not use a unique password, the hacker gains access to the e-mail account.
- Phishing e-mails that ask for account information or direct you to a phishing web-site. Don't dismiss this because the messages are a lot more convincing that you would imagine, often using text copied from actual Google e-mails or on-line forms.
- Use of a computer that is infected with a key-logger or other malware (most common for public computers like at a school or library) which records your login information.
When you reclaim Your Account:
Begin by scrolling to the bottom of your Gmail page and see if there are any other sessions signed into your account ("This account is open in 1 other location"). Then click the word "Details" where it says "Last account activity" and then "Sign out all other sessions". Now change your password to anything reasonable but without worrying too much about how secure because you are going to change it again. Next check all the following items and verify that they are set correctly.
Note: in the following “Settings” means “Mail settings” as found under the Gear icon in the upper/right of the Gmail window. If you still have the old layout, then “Settings” will be one of the choices along the top. If you have the older “Settings” link, some of the paths below will be slightly different.
Account Security:
- Settings -> Accounts and Import -> Change Account Settings -> Change Password [pick a new secure password]
- Settings -> Accounts and Import -> Change Account Settings -> Change password recovery options [verify secret question, SMS and recovery e-mail address]
- Settings -> Accounts and Import -> Change Account Settings -> Other Google account settings -> Email Address -> Edit [verify your name and other settings]
- Settings -> Accounts and Import -> Change Account Settings -> Other Google account settings -> Authorizing applications & sites [revoke Access to any sites listed]
- Settings -> Accounts and Import -> Change Account Settings -> Other Google account settings -> Using 2-step verification [enable 2-step verification]
Potential Spam:
- Settings -> General -> Signature [make sure nothing as been added]
- Settings -> General -> Vacation Responder [make sure it's disabled and empty]
E-mail Theft
- Settings -> Forwarding and POP/IMAP -> POP Download [disabled]
- Settings -> Forwarding and POP/IMAP -> IMAP Access [disabled]
- Settings -> Forwarding and POP/IMAP -> Forwarding [disabled or correct address]
- Settings -> Filters [no filters that forward or delete e-mail]
- Settings -> Accounts and Import -> Send Mail As [make sure it is using your correct e-mail address, delete any unrecognized entries]










